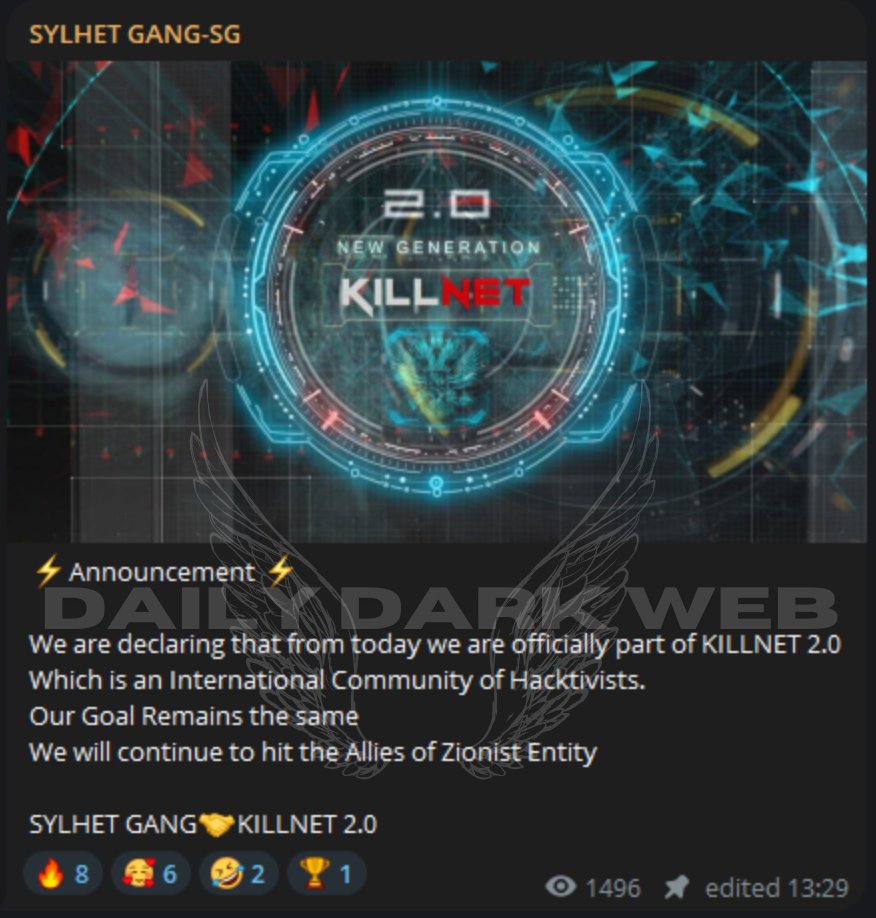
In a global hacking move, the Sylhet Gang-SG recently declared its allegiance to the notorious KillNet 2.0 hacker collective. This announcement ushers in a new era of cyber threats, particularly targeting allies of Israel.
KillNet 2.0, in a dark web statement, revealed its transformation into an international decentralized hacktivist group, emphasizing a diverse global membership with a focus on hardcore, targeted actions.
Describing itself as more than just a community but an idea fostering communities, KillNet 2.0 aims to unite hackers on the side of good from around the world.
The group explicitly shuns advertising, donations, or fees, highlighting its commitment to a decentralized approach to hacking activism.
The KillNet 2.0 Hacker Collective: The Threat of 2024
Following this development, Killmilk, a key player in the hacking world, introduced a new hacktivist group named Just Evil.
This move effectively divides the original Killnet into three factions, including Deanon retaining control over the original Killnet channel, Killnet 2.0 will be welcoming new member groups, emphasizing an international and decentralized structure, and Just Evil, linked to Killmilk, expanding the influence of the original Killnet.
The Cyber Express previously reported on the emergence of Killnet 2.0, a group challenging the conventional hierarchy of hacker communities.
Known for its proficiency in cyberattacks, the group has left its mark on the hacking industry with activities extending beyond mere notoriety.
Operating primarily on the dark web, KillNet 2.0’s illicit operations involve infiltrating systems and compromising sensitive information.
The Saga of KillNet Hacker Group
This pro-Russia hacker group gained infamy for its 2022 Denial-of-Service (DoS) and Distributed Denial-of-Service (DDoS) attacks during the Russian invasion of Ukraine.
Targeting global government institutions, the group’s activities prompted a warning from the Five Eyes intelligence alliance in April 2022.
As KillNet 2.0 solidifies its position, a previous instance in October 2023 indicates a surge in cyberattacks on Israeli government and media websites.
Various hacking groups, including those associated with Russia, have joined forces with the Palestinian military group Hamas.
Killnet, claiming to comprise patriotic Russian volunteer hackers, declared its intent to unleash distributed denial-of-service attacks on all Israeli government systems.
The group blames Israel for ongoing conflicts and accuses the country of supporting Ukraine and NATO.
Killnet proudly asserts its successful disruption of an Israeli government website and the security agency Shin Bet’s site, demonstrating its cyber capabilities.
Media Disclaimer: This report is based on internal and external research obtained through various means. The information provided is for reference purposes only, and users bear full responsibility for their reliance on it. The Cyber Express assumes no liability for the accuracy or consequences of using this information.

















