Tomb – A File Encryption Tool To Protect Your Secret Files In Linux

Tomb is a free and open source file encryption tool to protect your secret files in GNU/Linux operating systems. It allows the users to create a encrypted storage (a folder) in the file system and save the important data in it. The encrypted storage can be opened and closed using their associated keyfiles, which are also protected by a password chosen by the user. For the sake of security, you can save the keyfiles on a separate medium, say for example an USB drive or a CD/DVD. The encrypted folders are called “tombs”. You can create any number of tombs in your hard drive as long as it has enough free space. A tomb can only opened if you both have the keyfile and the password. It also has advanced features, like steganography, which allows you to hide the keyfiles within another file. Even though, Tomb is a CLI tool, it also has a GUI wrapper called gtomb, which makes the usage of Tomb much easier for the beginners.
In this brief tutorial, let us see how to install Tomb and how to use it to encrypt the files in Linux.
Tomb – A File Encryption Tool To Protect Your Secret Files
Install Tomb in Linux
Tomb will only work on GNU/Linux at this time.
On Arch Linux and derivatives:
In Arch Linux, Tomb is available in AUR. So, you can install it using AUR helper tools such as Yaourt or Packer as shown below.
yaourt -S tomb gtomb
Or,
packer -S tomb gtomb
On Debian, Ubuntu, Linux Mint:
SparkyLinux (A Debian derivative) developers have added Tomb package in their official repositories. So, you can install it by adding the SparkyLinux main repositories in your DEB based system.
To add SparkyLinux repositories in your Debian, Ubuntu, Linux Mint system, create a repository file:
sudo vi /etc/apt/sources.list.d/sparky-repo.list
Add the following lines:
deb https://sparkylinux.org/repo stable main deb-src https://sparkylinux.org/repo stable main deb https://sparkylinux.org/repo testing main deb-src https://sparkylinux.org/repo testing main
Save and close the file.
Install Sparky public key:
sudo apt-get install sparky-keyring
Or,
wget -O - https://sparkylinux.org/repo/sparkylinux.gpg.key | sudo apt-key add -
Then, update the source list using command:
sudo apt-get update
Finally, install tomb and gtomb using command:
sudo apt-get install tomb gtomb
For other Linux distributions, follow the steps provided here.
Usage
The command line way:
Like I said already, we call encrypted directory as “tomb”. Each tomb can be opened using their associated keyfile and password.
Let us create a new tomb, say for example ostechnix, with size 100MB. You need to be either root user or have sudo privileges to create tombs.
sudo tomb dig -s 100 ostechnix.tomb
Sample output:
tomb . Commanded to dig tomb ostechnix.tomb tomb (*) Creating a new tomb in ostechnix.tomb tomb . Generating ostechnix.tomb of 100MiB 100 blocks (100Mb) written. 100+0 records in 100+0 records out -rw------- 1 ostechnix ostechnix 100M Jul 4 18:53 ostechnix.tomb tomb (*) Done digging ostechnix tomb . Your tomb is not yet ready, you need to forge a key and lock it: tomb . tomb forge ostechnix.tomb.key tomb . tomb lock ostechnix.tomb -k ostechnix.tomb.key
Create a keyfile used to lock the newly created tomb.
sudo tomb forge ostechnix.tomb.key
Note: If you encountered an error like below, there might an active swap partition.
tomb . An active swap partition is detected... [sudo] password for ostechnix: tomb [W] This poses a security risk. tomb [W] You can deactivate all swap partitions using the command: tomb [W] swapoff -a tomb [W] [#163] I may not detect plain swaps on an encrypted volume. tomb [W] But if you want to proceed like this, use the -f (force) flag. tomb [E] Operation aborted.
Deactivate all swap partitions to fix this as shown below.
sudo swapoff -a
And, then re-run the command to create keyfile. It will some time. After few minutes, you’ll be asked to enter a new password to secure the key. Enter it twice.
We have just created a keyfile.
Run the following command to lock the tomb using the keyfile:
sudo tomb lock ostechnix.tomb -k ostechnix.tomb.key
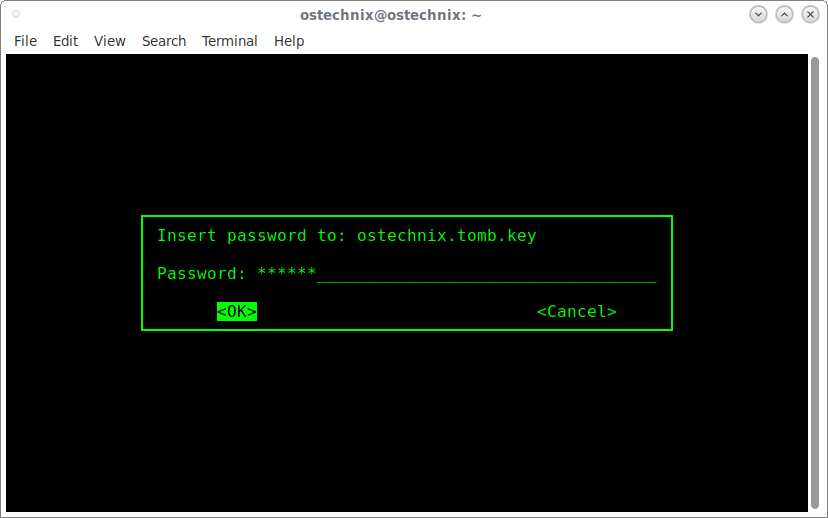
You will be asked to enter a password to your.tomb.key file:
After entering a password, you’ll see an output something like below.
tomb . Commanded to lock tomb ostechnix.tomb [sudo] Enter password for user ostechnix to gain superuser privileges tomb . Checking if the tomb is empty (we never step on somebody else's bones). tomb . Fine, this tomb seems empty. tomb . Key is valid. tomb . Locking using cipher: aes-xts-plain64:sha256 tomb . A password is required to use key ostechnix.tomb.key tomb . Password OK. tomb (*) Locking ostechnix.tomb with ostechnix.tomb.key tomb . Formatting Luks mapped device. tomb . Formatting your Tomb with Ext3/Ext4 filesystem. tomb . Done locking ostechnix using Luks dm-crypt aes-xts-plain64:sha256 tomb (*) Your tomb is ready in ostechnix.tomb and secured with key ostechnix.tomb.key
Now, we have a 100MB tomb called “ostechnix”, and locked it down using a keyfile, which is also protected by a password.
Since this is just demonstration purpose. I have stored the keyfile and tomb in the same directory (my $HOME directory). For the sak of security, you shouldn’t keep your keys where your tomb is! If you have stored the keyfile in a different path or medium, you need to mention the correct the path value of keyfile while opening the tombs.
To open the tomb, run:
sudo tomb open ostechnix.tomb -k ostechnix.tomb.key
Enter the password to your keyfile:
After entering the valid password, you will see the following output:
tomb (*) Success unlocking tomb ostechnix tomb . Checking filesystem via /dev/loop0 fsck from util-linux 2.27.1 ostechnix: clean, 11/25168 files, 8831/100352 blocks tomb (*) Success opening ostechnix.tomb on /media/ostechnix
Congratulations! The tomb has been mounted under /media directory (i.e /media/ostechnix in my case).
Now, you can save your secret files/folders in this tomb (i.e encrypted directory). Again, you need to be sudo or root user to save the data in this tomb.
Once you are done, close it using command:
sudo tomb close
Sample output:
tomb . Closing tomb [ostechnix] mounted on /media/ostechnix tomb (*) Tomb [ostechnix] closed: your bones will rest in peace.
If you are in a hurry, you can forcibly close all open tombs using command:
sudo tomb slam all
The above command will immediately close all open tombs, killing all applications using them. We can use multiple tombs at the same time. All directories and files inside them can be bound to files and directories inside your $HOME, placing all configurations where the applications expect them.
For more usage details, refer the official guide.
The graphical way:
If you don’t comfortable with the command line, you can use Gtomb, the GUI wrapper for Tomb.
Launch it from the Menu. This is how gtomb default interface looks like.
As you see in the above screenshot, all options are self-explanatory.
To create a tomb, choose the first option dig, and click OK. Choose the location where you want to keep the tomb.
Next, enter the size of your tomb:
Next, we need to create keyfile which is used to lock down the the tomb. Choose forge from the main menu and click OK. Enter passphrase twice.
Next, choose lock from the main menu to lock down the tomb using the newly created key file. To open the tomb, choose open from the main menu and choose the tomb. As you can see, gtomb usage is fairly easy and straight forward. You don’t have memorize all commands. You can do everything with few mouse clicks.
And, that’s all for now. I hope this helps. As far as I tested, Tomb is one of the useful tool ever I have used. It helps you to secure your secret files in an encrypted directory. Give it a try, you won’t be disappointed.
Cheers!
Resource:
Thanks for stopping by!
Help us to help you:
- Subscribe to our Email Newsletter : Sign Up Now
- Support OSTechNix : Donate Via PayPal
- Download free E-Books and Videos : OSTechNix on TradePub
- Connect with us: Facebook | Twitter | Google Plus | LinkedIn | RSS feeds
Have a Good day!!