Remote management features that have shipped with Intel processors for almost a decade contain a critical flaw that gives attackers full control over the computers that run on vulnerable networks. That's according to an an advisory published Monday afternoon by Intel.
Intel has released a patch for the vulnerability, which resides in the chipmaker's Active Management Technology, Intel Small Business Technology, and Intel Standard Manageability. Business customers who buy computers running vPro processors use those services to remotely administer large fleets of computers. The bug doesn't affect chips running on consumer PCs. The chipmaker has rated the vulnerability critical and is recommending vulnerable customers install a firmware patch.
In the company's Monday post, Intel officials wrote:
There is an escalation of privilege vulnerability in Intel® Active Management Technology (AMT), Intel® Standard Manageability (ISM), and Intel® Small Business Technology versions firmware versions 6.x, 7.x, 8.x 9.x, 10.x, 11.0, 11.5, and 11.6 that can allow an unprivileged attacker to gain control of the manageability features provided by these products. This vulnerability does not exist on Intel-based consumer PCs.
There are two ways this vulnerability may be accessed please note that Intel® Small Business Technology is not vulnerable to the first issue.
- An unprivileged network attacker could gain system privileges to provisioned Intel manageability SKUs: Intel® Active Management Technology (AMT) and Intel® Standard Manageability (ISM).
- CVSSv3 9.8 Critical /AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
- An unprivileged local attacker could provision manageability features gaining unprivileged network or local system privileges on Intel manageability SKUs: Intel® Active Management Technology (AMT), Intel® Standard Manageability (ISM), and Intel® Small Business Technology (SBT).
- CVSSv3 8.4 High /AV:L/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
The flaw affects Intel manageability firmware versions 6.x, 7.x, 8.x 9.x, 10.x, 11.0, 11.5, and 11.6 for Intel's Active Management Technology, Small Business Technology, and Standard Manageability platforms. Versions before 6 or after 11.6 are not impacted.
Security experts spent much of Monday assessing the real-world threat posed by the bug. A post published earlier in the day claimed "every Intel platform from Nehalem to Kaby Lake [had] a remotely exploitable security hole" that had gone unfixed for years. Researchers who parsed Intel's advisory, however, said the flaw could likely be exploited over the Internet only when Intel's AMT service was enabled and provisioned inside a network.
Other researchers said the bar for unprivileged network attackers to succeed was probably even higher because Windows-based software known as Local Manageability Service would have to be running.
"It sounds like its only remotely exploitable if the LMS service is running on the affected system (even if AMT is enabled, LMS is the network vector)," HD Moore, who is vice president of research and development at Atredis Partners, told Ars. "Only servers running that service (vs. desktop PCs) with the port reachable are exposed to remote code execution."
Moore said a query using the Shodan computer search engine detected fewer than 7,000 servers showing they had ports 16992 or 16993 open. Having those ports open is a requirement for the remote attack. That number of servers still represents a potentially substantial threat because tens of thousands of computers could be connected to some of those hosts. Enterprises that have LMS and AMT enabled in their networks should make installing the patch a priority. Those organizations that can't immediately install updates should follow these workaround instructions.
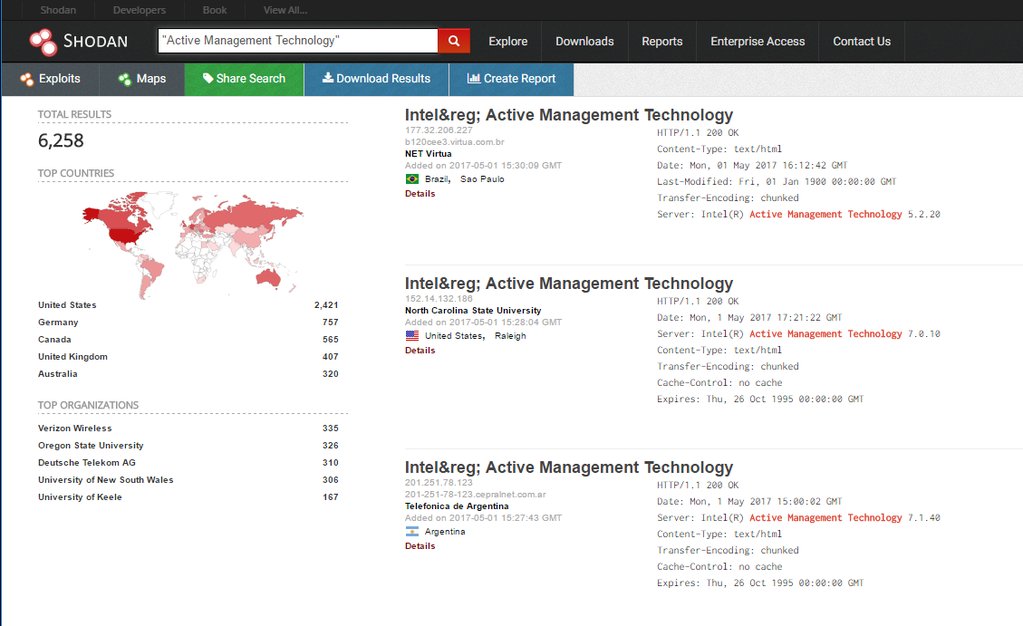
As indicated in Intel's advisory, a second, less-serious threat is a local privilege escalation once an attacker already has low-privilege access. While not as severe as the first scenario, this threat could still make it much easier for an attacker to take control of targeted computers inside a network. Vulnerable organizations should patch as soon as practical. Developer Matthew Garrett has more information about the vulnerability here.
You must login or create an account to comment.